Subscribe to:
Post Comments (Atom)
Archives for RSS Returns : History as Seen by Bloggers "I would rather have questions that can't be answered than answers that can't be questioned" Richard Feynman "The penalty good people pay for not being interested in politics is to be governed by people worse than themselves." - Plato, Greek philosopher.
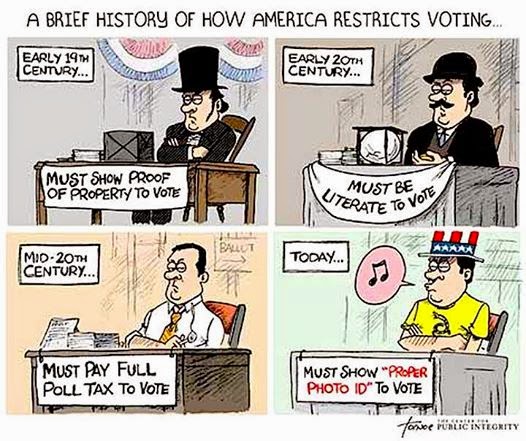
Classified Conspiracy Theory

Search This Blog
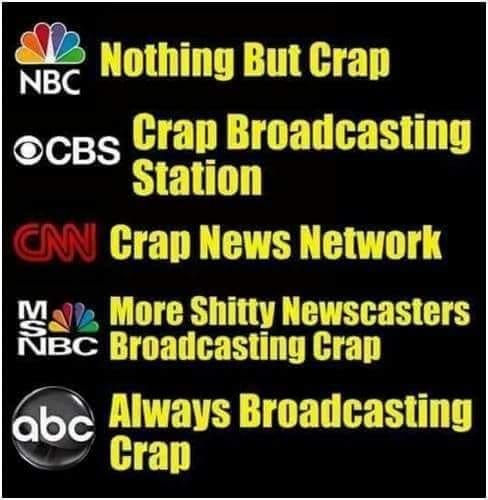
Media Consolidation
Fair Use Notice
WARNING for European visitors: European Union laws require you to give European Union visitors information about cookies used on your blog. In many cases, these laws also require you to obtain consent. As a courtesy, we have added a notice on your blog to explain Google's use of certain Blogger and Google cookies, including use of Google Analytics and AdSense cookies. You are responsible for confirming this notice actually works for your blog, and that it displays. If you employ other cookies, for example by adding third party features, this notice may not work for you. Learn more about this notice and your responsibilities.
Search This Blog
One Planet

Free Country
Noted Articles
Search published scientific literature
You.com ( ad free Search )
Why Craig Kelly resigned on Tuesday ( post FB censorship)
Barrington Declaration ( ripping a strip off Covid-19 policy)
Collateral Global Project studying outcomes of policies
A Henchman Balks : Digby ( Is it sad...or hysterically funny?)
Livejournal - RSS Syndication
Korean professor on COVID-19 ( likes masks)
Sidebar lists of Notable Articles - Livejournal - Tagfile
SIDEBAR INDEX - Notable Articles reposted to LiveJournal
Disqus : o.p.i.t.
Public Dashboard : opit RSS Netvibes 2 3 4 5
Book Love Foundation
Civil Newsrooms : Blockchain
Seen This : About ( French )
Fossil Fuel Subsidies ( kindly find them )
When feeding the desperate becomes a crime ( despicable law)
https://file.wikileaks.org/file/ ( Assange arrest 'celebration' )
Religious Discrimination Bill : Australia ( lawyer employment initiative )
Aquatic Ape Pt 1 ( YouTube )
Ambassador of Controversy : Pt 1 Craig Murray
The Bremer Edicts ( Iraq )
300 free online courses from Ivy League universities
Secretmag.ru BookBub Signs of the times DQ World
Secretmag.ru BookBub Signs of the times DQ World
The Knockout Punch The real climate record explained
YouTube Censorship Defends Powerful ( Watch the clip )
Floodgap HT Opera
Body Count pdf
IDEAS Economics Research Database - Federal Reserve
anh

Pages
NSA was so secret its name was hidden

BiPartisan Tyranny

History of Education

Clean Coal


Clustermap
Translate
Blog Archive
-
▼
2017
(1155)
-
▼
February
(61)
- 28 February - Blogs I'm Following
- 27 Feb - Blogs I'm Following
- 27 February - My Feedly!
- 26 February - Blogs I'm Following
- 26 February - igoogle portal - old 2
- 26 February - igoogle portal - old
- 26 February - igoogle portal
- 26 February - Netvibes - oldephartteintraining
- 26 February - My Yahoo! II
- 26 February - My Yahoo!
- 26 February - Pale Moon START Page
- 25 February - Blogs I'm Following
- 24 February - Blogs I'm Following
- 23 February - Blogs I'm Following
- 22 February - Blogs I'm Following
- 21 February - Blogs I'm Following
- 20 February - Blogs I'm Following Part 2
- 20 February - Blogs I'm Following
- 20 February - igoogle portal - old #2
- 20 February - igoogle portal - old
- 20 February - igoogle portal ( + some Disqus Notes )
- 20 February - Netvibes - oldephartteintraining
- 20 February - My Yahoo! - 2
- 20 February - My Yahoo!
- 20 February - Pale Moon START Page - News and Tech...
- 19 February - Blogs I'm Following
- Anti-Religion ; state mindwashing to promote state...
- 18 February - Blogs I'm Following
- 17 February - Blogs I'm Following
- 16 February - Blogs I'm Following
- 15 February - Blogs I'm Following
- 14 February - Blogs I'm Following
- 13 February - Blogs I'm Following
- 12 February - Blogs I'm Following
- 11 February - Blogs I'm Following
- 11 February - igoogle portal - old #2
- 11 February - igoogle portal - old
- 11 February - igoogle portal
- 11 February - Netvibes - oldephartteintraining
- 11 February - My Yahoo! - 2
- 11 February - My Yahoo!
- 11 February - Pale Moon START Page
- 11 February - Opera START Page
- 10 February - Blogs I'm Following
- 9 February - Blogs I'm Following
- 8 February - Blogs I'm Following
- 7 February - Blogs I'm Following
- 6 February - Blogs I'm Following
- 5 February - Blogs I'm Following
- 4 February - Blogs I'm Following
- 4 February - igoogle portal - old - 2
- 4 February - igoogle portal - old
- 4 February - igoogle portal
- 4 February - Netvibes - oldephartteintraining
- 4 February - My Yahoo! 2
- 4 February - My Yahoo!
- 4 February - Pale Moon START Page - News and Tech ...
- 4 February - New Opera START Page
- 3 February - Blogs I'm Following
- 2 February - Blogs I'm Following
- 1 February - Blogs I'm Following
-
▼
February
(61)
About Me
- opit
- I've been 'around' for a few years now, pursuing the shifting goal of a sharable home-made surfers resource site focused on ease of use and variety of mostly adult ( whoa : I didn't say prurient ) content.





No comments:
Post a Comment